MAXIMIZING SECURITY IN WINDOWS 365: LEVERAGING CITRIX ZERO TRUST

The shifting dynamics of workplace environments, where remote work has become more prevalent, the importance of robust cybersecurity measures has never been more critical. In the context of these changes, companies using Windows 365 are increasingly turning to Citrix Zero Trust solutions to enhance their security postures.
This strategic combination allows organizations to leverage the cloud's flexibility while ensuring that their applications and data remain secure against evolving threats. At its core, the Zero Trust model adheres to a simple principle: "Never trust, always verify." This is a shift from traditional security models which operated on the assumption that everything inside the organization’s network should be trusted. In contrast, Zero Trust assumes that threats can be internal or external and thus verifies each request as if it originates from an open network.
This article will delve deep into how integrating Citrix Zero Trust with Windows 365 can significantly fortify an organization’s security framework, discussing both theoretical aspects and practical implementations. By the end, readers will have a comprehensive understanding of applying these technologies together to maximize security and operational efficiency.
Understanding the Basics of Citrix Zero Trust and Windows 365
Citrix Zero Trust is not a product but an approach to cybersecurity that can be implemented through various Citrix solutions. These include Citrix Workspace and Citrix Secure Internet Access, which offer different layers of security and access controls.
Citrix's technology supports Zero Trust by providing fine-grained access control and ongoing monitoring and response operations, which adapt protections based on user behaviors and threats.
Windows 365, Microsoft's cloud-based service, brings the Windows operating system to the Microsoft cloud, streaming the full Windows experience — apps, data, and settings — to personal and corporate devices.
This model supports business flexibility but also opens up new vectors for security vulnerabilities if not properly managed. When Citrix Zero Trust is implemented with Windows 365, the architecture enforces security policies at every access point. For instance, even if a device is compromised, the integrity of the system and data within the Windows 365 environment can still be preserved, making it an exceedingly robust framework against a variety of cyber threats.
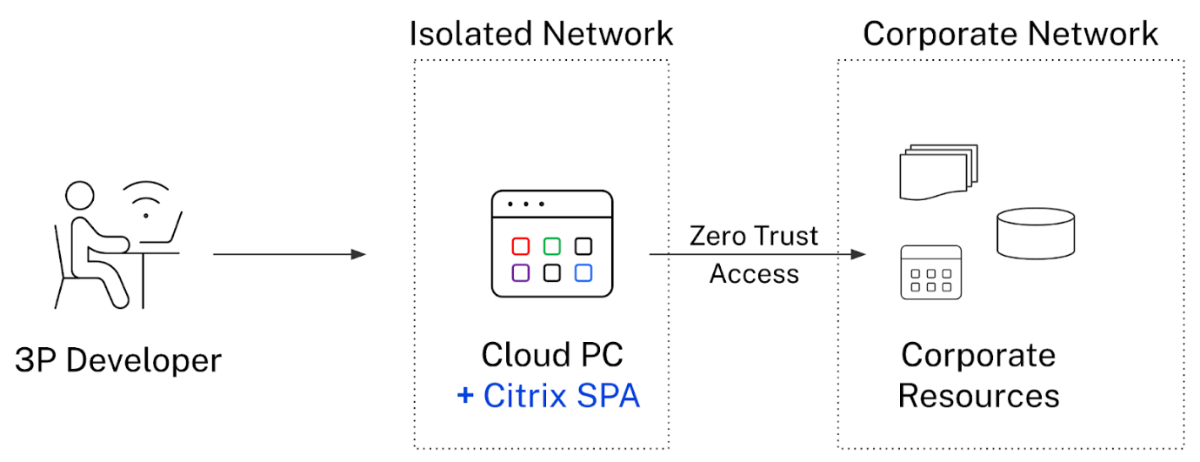
Key Benefits of Integrating Citrix Zero Trust with Windows 365 Enhanced Data Security: By continuously validating every request, Citrix Zero Trust helps ensure that only authenticated and authorized users and devices can access Windows 365 applications and data.
- Reduced Surface Attack: Adopting a Zero Trust model inherently minimizes the attack surfaces since the network is segmented and controls are dynamically enforced.
- Adaptive Controls: With Citrix, policies and protections evolve based on user behavior and context, which means security is never static and adapts to potential threats proactively.
- Regulatory Compliance: Many industries face stringent regulatory requirements regarding data protection and privacy. Implementing Citrix Zero Trust with Windows 365 can aid in compliance by providing robust safeguards and audit trails.
Practical Steps to Implement Zero Trust with Windows 365 Implementing Zero Trust with Windows 365 involves a series of strategic and technical steps designed to create a secure and efficient work environment:
- User Verification: Every user must be authenticated using multiple factors before being granted access to any resources in Windows 365.
- Device Security: All devices used to access Windows 365 must be in compliance with the organization's security policies. This may include ensuring the device is not jailbroken/rooted, is up to date with patches, and has endpoint security solutions installed.
- Least-Privilege Access: Users should have the minimum level of access necessary to perform their tasks. This limits potential damage should their credentials be compromised.
- Micro segmentation: Dividing the network into smaller zones helps in controlling sensitive data and systems more closely and isolate them in the event of a breach.
- Real-Time Analytics: Employing tools like Citrix Analytics for Security can provide insights into user behavior to detect anomalies and automatically adjust access controls accordingly.
Challenges and Considerations
While the integration of Citrix Zero Trust with Windows 365 offers significant security enhancements, organizations might face several challenges during its implementation.
These include:
- Complexity in deployment,
- initial costs, and the need for ongoing management and fine-tuning of security policies.
- User education is critical, as stakeholders must understand the necessity of stringent controls and compliance requirements.
To overcome these challenges, it is advisable to phase the implementation, starting with critical assets first and gradually expanding coverage. Regular training sessions and updates should also be part of the deployment strategy to facilitate smooth adaptation by all users.
Conclusion
In conclusion, combining Citrix Zero Trust architecture with Windows 365 offers organizations a powerful solution to secure their digital environments in a world where traditional security perimeters no longer suffice.
By rigorously verifying and limiting access, organizations can both enhance their security postures and comply with regulatory demands. Effective implementation of this combined approach ensures that businesses can continue to thrive in the digital age while protecting their critical assets against sophisticated cyber threats.