NETSCALER FILE INTEGRITY MONITORING.

NetScaler File Integrity Monitoring NetScalerⓇ has introduced a new feature within Application Delivery Management (ADM) Service called File Integrity Monitoring that will help determine if changes have been made to a NetScaler build files.
The challenge: Unapproved changes in a NetScaler build files.
Even when all precautions to prevent unapproved changes have been taken to the core build files for NetScaler, subtle manipulation of these files can go unnoticed, allowing attackers to operate undetected.
Compounding this problem is the sheer volume of files within NetScaler. Monitoring each of these files for changes manually is an enormous task, prone to error, and often insufficient for detecting subtle or rapid alterations. Even with existing security measures in place, the dynamic nature of cyber threats demands a more proactive approach to identifying unauthorized modifications to your NetScaler build files.
NetScalerⓇ File Integrity Monitoring provides valuable insights that help manage this risk.
The response: NetScaler File Integrity Monitoring
NetScaler File Integrity Monitoring proactively identifies any changes in the very core of NetScaler ADCs — the build files.
How it works:
NetScaler File Integrity Monitoring examines the integrity of the NetScaler build files. Think of it as a digital fingerprint: NetScaler will compare the binary hash value of the current NetScaler build against the original binary hash linked to the same NetScaler build.
Discrepancies in the NetScaler build files identified by this feature will be flagged for attention.
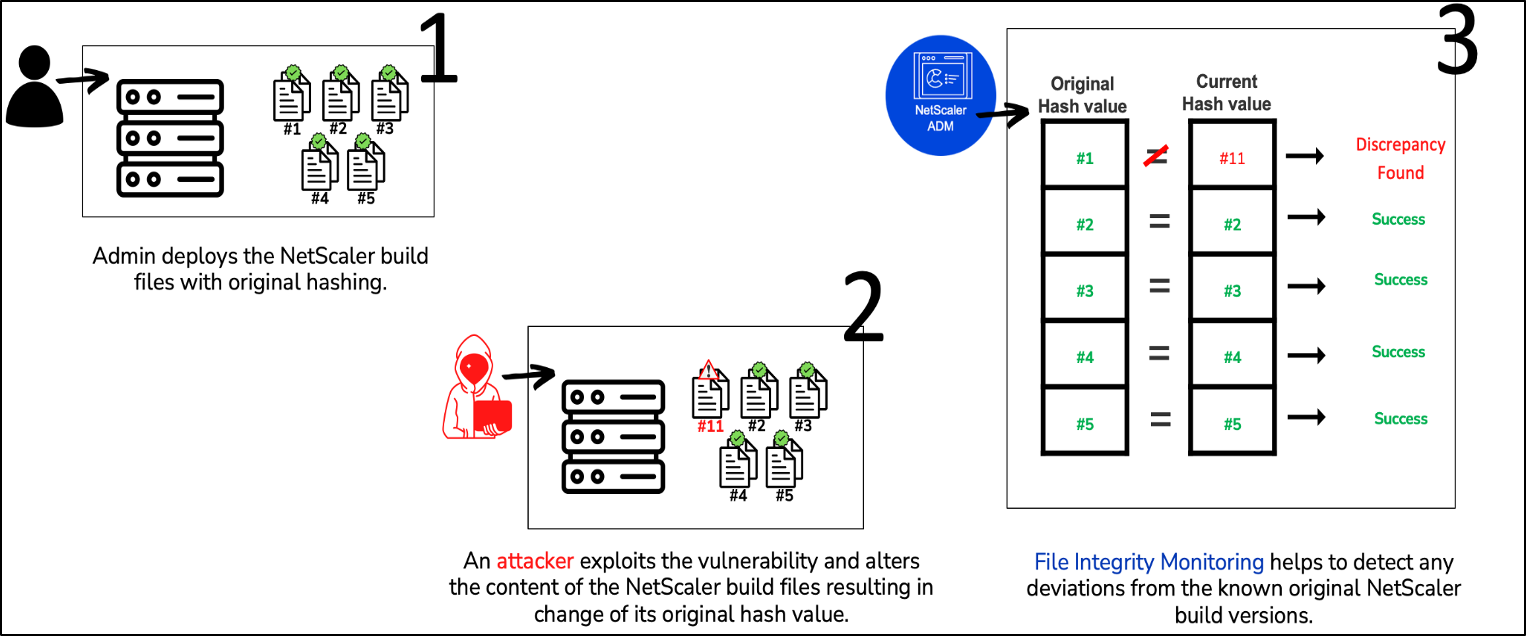
1. On-demand scan: Run file integrity scans as needed.
2. Reliable comparisons: NetScaler ADM stores the original binary hashes of files across all NetScaler build releases and compares them against the existing NetScaler files. Any detected deviation raises a red flag for further investigation. Please proceed with the organization's digital forensics procedure if any changes are flagged.
3. File altered, and file added: File Integrity Monitoring helps detect changes in the existing NetScaler build files as well as files added to your NetScaler build.
How to use File Integrity Monitoring
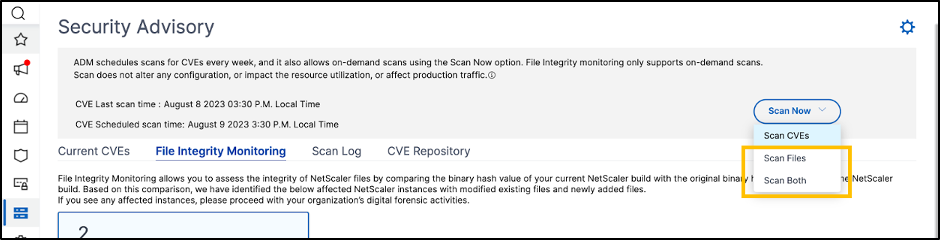
Go to the Security Advisory section of the NetScaler Application Delivery Management dashboard, click the File Integrity Monitoring tab, and run an on-demand scan:
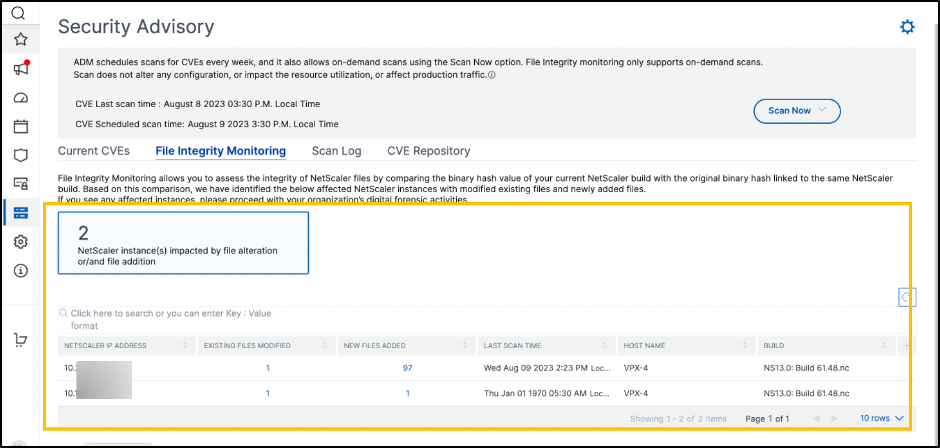
View the identified NetScaler ADCs and the list of files that were changed or added:
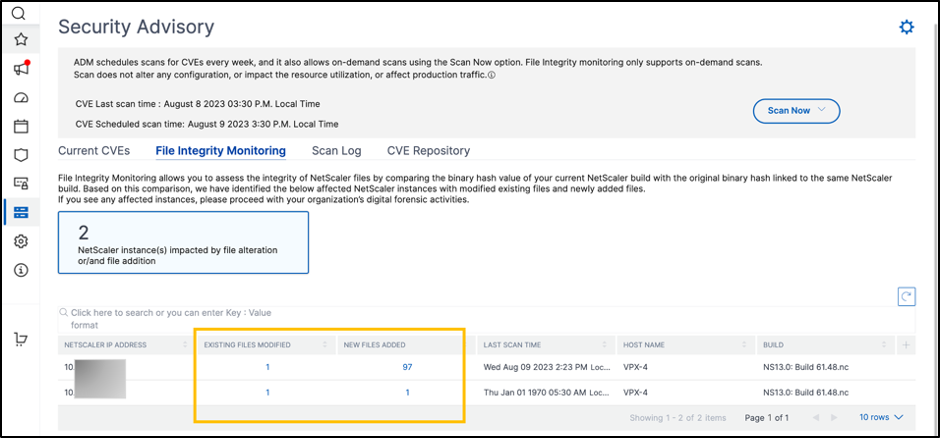
Click the existing files that were modified or on the newly added files to see the impacted file names:
This proactive approach will help detect file changes early, allowing for immediate action to secure the NetScaler ADCs.
To learn more about NetScaler File Integrity Monitoring, refer to the documentation.
Note that File Integrity Monitoring is available only with the cloud-hosted NetScaler Application Delivery Management (ADM) Service. If required, please contact OAS today.
DISCLAIMER
Please note that NetScaler File Integrity Monitoring (“the Feature”) is not capable of detecting all techniques, tactics, or procedures (TTPs) threat actors may use when targeting relevant environments. Threat actors change TTPs and infrastructure frequently, and therefore the Feature may be of limited to no forensic value as to certain threats. You are strongly advised to retain the services of experienced forensic investigators to assess your environment in connection with any possible threat. This document and the information contained in it is provided as-is. Cloud Software Group, Inc. makes no warranties or representations, whether express or implied, regarding the document or its contents, including, without limitation, that this document or the information contained in it, is error-free or meets any conditions of merchantability or fitness for a particular purpose.