OAS EXPLAINS - HOW ZERO TRUST SECURITY PROTOCALS WORKS

Detailed Explanation of the Mechanisms of Zero Trust Security Protocols
Introduction
Zero Trust is a security strategy built on the premise that no user, device, or network segment should be inherently trusted.
Every access request is treated as though it originates from an untrusted network, and must be authenticated, authorized, and encrypted before granting resource access. Traditional “castle-and-moat” defenses have given way to dynamic, identity-centric controls that continuously verify trust.
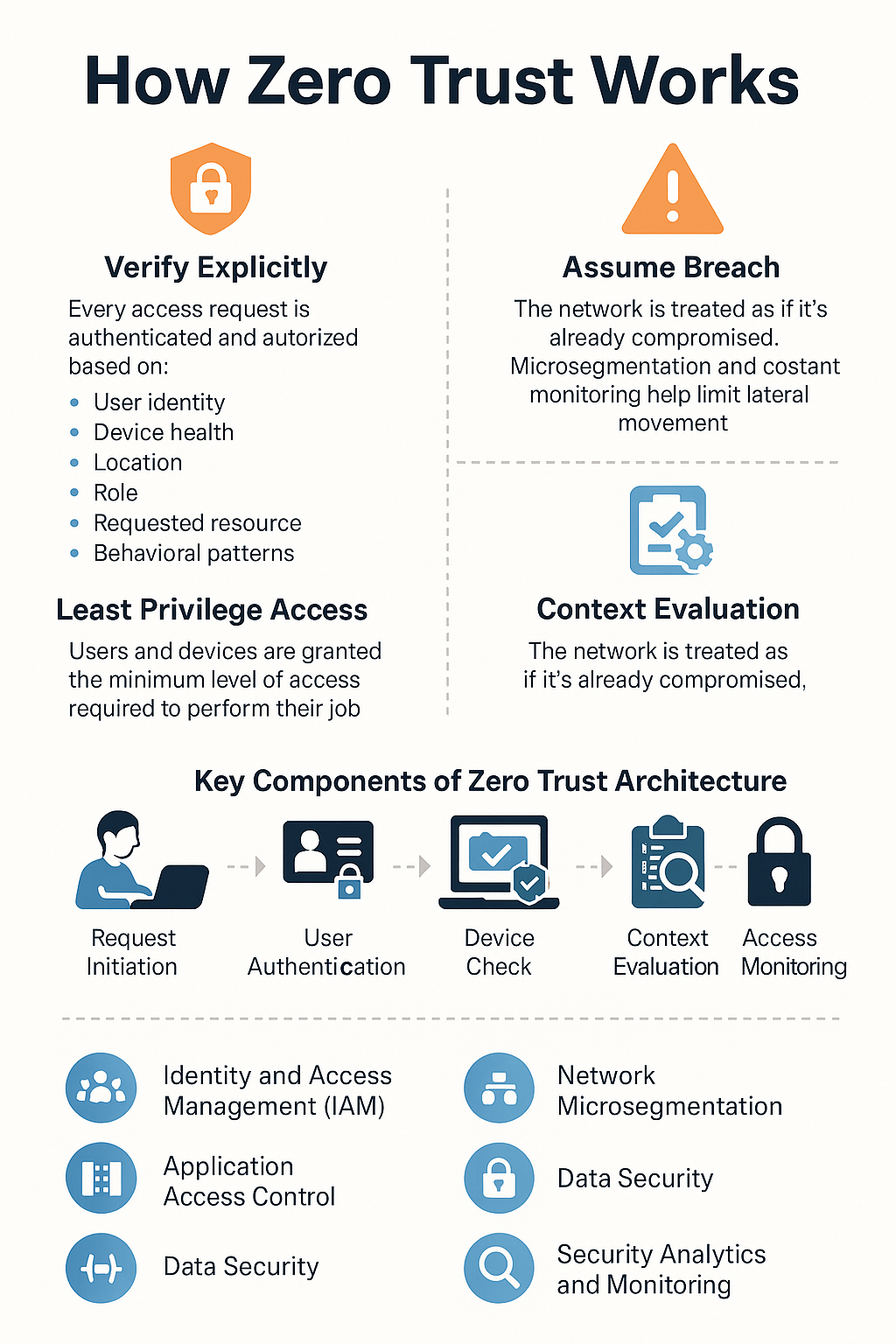
Core Principles
- Verify explicitly
Always authenticate and authorize based on all available data points, including user identity, device health, location, and behavioral patterns. - Use least privilege access
Limit user and system privileges to the minimum necessary. Employ Just-In-Time (JIT) and Just-Enough-Access (JEA) to reduce potential attack surfaces. - Assume breach
Operate under the assumption that attackers are already in the environment. Minimize blast radius through segmentation, end-to-end encryption, and continuous monitoring to quickly detect and contain incidents.
Identity and Access Management
Effective Zero Trust relies on a robust Identity and Access Management (IAM) framework:
- Multi-Factor Authentication (MFA) ensures that stolen or weak credentials alone cannot grant access.
- Single Sign-On (SSO) improves usability and centralizes policy enforcement.
- Adaptive authentication dynamically adjusts requirements based on context (e.g., location changes, device anomalies).
- Identity providers (IdP) and federation protocols (SAML, OAuth, OpenID Connect) issue and validate tokens that carry trust attributes.
Device Trust and Posture Assessment
Devices must meet organizational security standards before receiving any level of access:
- Maintain an up-to-date inventory of all endpoints, including laptops, mobile devices, IoT devices, and servers.
- Perform posture checks (e.g., OS patch level, antivirus status, encryption enabled) via Mobile Device Management (MDM) or Endpoint Detection and Response (EDR) tools.
- Deny or restrict access for non-compliant or unknown devices, ensuring only verified hardware interacts with sensitive resources.
Micro-Segmentation and Network Controls
Rather than one flat network, Zero Trust subdivides infrastructure into isolated segments:
- Each segment enforces its own access policies and inspection controls.
- Segmentation Gateways (SG) or next-generation firewalls mediate east-west traffic between workloads.
- Granular policies tie network flows to identity and device attributes, reducing lateral movement opportunities for attackers.
Continuous Monitoring and Analytics
Zero Trust thrives on real-time visibility and automated response:
- Collect logs from identity systems, endpoints, network devices, and applications.
- Use Security Information and Event Management (SIEM) and User and Entity Behavior Analytics (UEBA) to detect anomalies.
- Implement risk-based adaptive policies that re-evaluate sessions on events like failed logins, new software installs, or suspicious traffic patterns.
Encryption and Data Protection
Protecting data at every stage is fundamental:
- Enforce end-to-end encryptions for all communications—whether over public internet or internal networks—to prevent eavesdropping and tampering.
- Apply encryption at rest for sensitive databases and file stores, using Key Management Services (KMS) and Hardware Security Modules (HSM).
- Combine encryption controls with Attribute-Based Access Control (ABAC) to dynamically grant data access based on user role, device posture, and data sensitivity.
Implementation Architecture and Protocols
Zero Trust architectures typically comprise:
- Policy Decision Point (PDP): Evaluates requests against centralized policies.
- Policy Enforcement Point (PEP): Enforces the decisions on network gateways, application proxies, or endpoint agents.
- Trust Broker: Orchestrates communication between PDP and PEP, often leveraging APIs and standardized protocols (e.g., REST, gRPC).
- Identity Token Exchange: Uses OAuth 2.0, SAML assertions, or JSON Web Tokens (JWT) to carry claims about user identity and device posture.
- Secure Tunnel or Service Mesh: Creates encrypted channels (mTLS, TLS 1.3) for workload-to-workload communication.
Summary of Mechanisms
| Mechanism | Description | Example |
|---|---|---|
| Verify Explicitly | Authenticate and authorize every request using contextual data | MFA, adaptive risk policies |
| Least Privilege Access | Grant only necessary permissions, with Just-In-Time and Just-Enough-Access | Role-Based Access Control (RBAC) |
| Micro-Segmentation | Divide network into isolated zones with individual policies | VLANs, SGs, next-gen firewalls |
| Device Posture Assessment | Validate device compliance before granting any access | MDM checks, EDR health reporting |
| Continuous Monitoring and Analytics | Real-time logging and behavior analysis to detect anomalies | SIEM, UEBA |
| Encryption and Data Protection | End-to-end encryption and data-at-rest safeguards | TLS 1.3, disk encryption, ABAC rules |
Zero Trust is not a one-off project but an evolving strategy. As attackers adapt, organizations must continuously refine policies, integrate new telemetry, and automate enforcement. A common next step is adopting a Zero Trust maturity model to baseline current capabilities and chart a phased path toward full implementation.